sFlow Traffic Visibility for Industrial Networks|Complementing SNMP/Syslog
In industrial network environments, cybersecurity is no longer limited to firewalls and access control policies. As network architectures become more complex and device counts surge—while attack techniques keep evolving—the ability to monitor traffic behavior and detect anomalies in real time has become a critical challenge for administrators.
To address this, EtherWAN industrial switches are introducing a visualized traffic monitoring technology — sFlow — to complement existing SNMP and Syslog capabilities and deliver comprehensive network visibility and security.
Why SNMP / Syslog Alone Isn’t Enough
Administrators typically rely on SNMP (for device health and status) and Syslog (for event and change logging). However, when abnormal traffic or attacks occur—such as DDoS, internal misuse, or protocol anomalies—these tools lack packet-level visibility and may not provide the detail needed to pinpoint root causes quickly.
- SNMP: Ideal for device-level monitoring (CPU usage, uptime, interface status), but limited insight into traffic behavior.
- Syslog: Excellent for event tracking and auditing, yet primarily text-based with limited visualization.
What Is sFlow?
sFlow (Sampled Flow) is a standardized traffic-monitoring protocol (RFC 3176). It collects data via packet sampling and interface statistics, then actively pushes the data over UDP to an sFlow Collector for analysis and visualization.
Core Components
- sFlow Agent: Embedded in switches/routers, periodically exports Flow Samples (packet snapshots) and Counter Samples (interface counters).
- sFlow Collector: Receives and analyzes sFlow datagrams, turning them into dashboards and reports for anomaly detection and capacity planning.
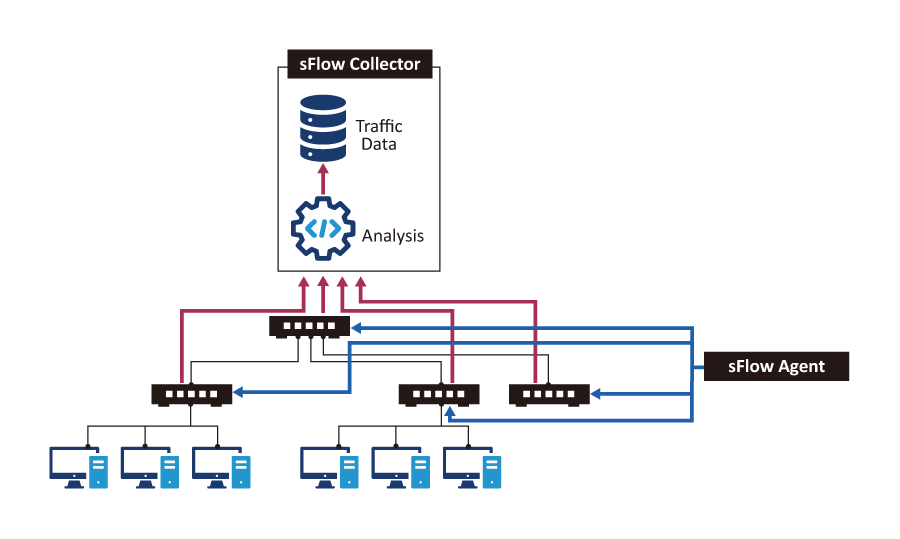
Dual Sampling: Traffic Behavior + Device Statistics
- Flow Samples: Source/destination IP, ports, protocol types, and flow direction—vital for DDoS detection, application/protocol analysis, and misuse investigation.
- Counter Samples: Packet counts, error rates, interface utilization—useful for performance monitoring and capacity planning.
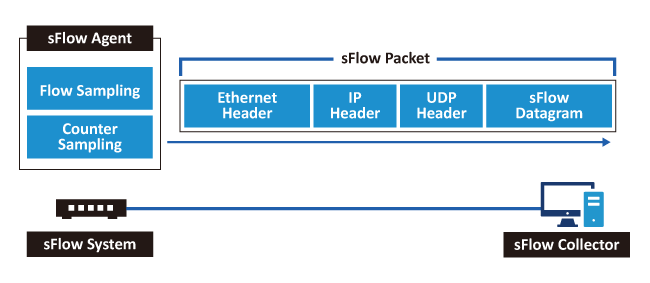
Both sample types can be encapsulated in a single sFlow UDP datagram, providing a holistic view of network activity and device status.
sFlow × SNMP × Syslog: Complementary Roles
| Aspect | sFlow | SNMP | Syslog |
|---|---|---|---|
| Transport Method | Push (active sampling & export) | Pull (polling) | Push (event-triggered logs) |
| Data Type | Traffic details + interface statistics | Device status & performance | System events & messages |
| Real-Time Capability | High (continuous export) | Moderate (polling interval) | High (events logged instantly) |
| Security Monitoring | High (traffic anomalies, DDoS) | Basic (device health) | Moderate (event tracking) |
| Visualization Support | Strong (flows, trends, ingress/egress) | Weak (needs external tools) | Weak (text-based) |
| Packet-Level Visibility | Yes | N/A | N/A |
| Device-Level Monitoring | Partial (interface counters) | Yes | N/A |
| Event Logging | N/A | N/A | Yes |
| Anomaly Detection | Yes (real-time traffic anomalies) | N/A | Partial (with SIEM/analytics) |
| Standards | RFC 3176 | SNMPv1/v2c/v3 | RFC 5424 |
| Typical Use Cases | Traffic analysis, anomaly detection, QoS | Device monitoring, network management | Event/audit logging, troubleshooting |
Cybersecurity & Operations Use Cases
- DDoS Detection & Mitigation: Real-time spike detection with threshold-based alerts; apply ACLs or blackhole routing when needed.
- Internal Misuse Analysis: Visualize abnormal patterns (excessive connections, unusual protocols) to aid investigations.
- Traffic Trend Forecasting & QoS: Long-term statistics inform capacity planning and policy tuning to stabilize critical services.
- Real-Time Visualization & Troubleshooting: More immediate traffic insight than SNMP polling, accelerating root-cause analysis.
Conclusion
sFlow is not a replacement for SNMP or Syslog—it complements them by filling the traffic-level visibility gap. Together, they form a complete MMA (Monitoring, Management & Analysis) framework: monitor device health, log system events, and analyze traffic behavior in real time.
EtherWAN will leverage sFlow-based visibility to help industrial networks maintain high availability and strong security in complex, mission-critical environments.